[REPORT] Mail notification received from access point.
Subject: YoRHa_CLASSIFIED_12u3440029491
Origin: Bunker
Query: What is the nature of this transmission?
Hypothesis: A deeper analysis of the enclosed files may yield more information.
Proposal: A scanner-type unit is advised to perform standard scanning procedures on the data for further analysis and conclusions.
Warning: Data appears to be classified. Any actions related to hacking or unauthorized transactions could be associated with treason. The unit is advised to perform such acts in secrecy.
Tools Used
- file
- WinDBG
- keepass-password-dumper
- CyberChef
Approach
Initial Analysis
Upon extracting the challenge zip file, I encountered two files: “Bunker_DB” and “Bunker_DMP.” My first thought was that one was a database file and the other was a memory dump. I ran the file command to identify the specifics, revealing a Mini DuMP crash report and a KeePass 2.x KDBX database.
Enumeration
Knowing the file types and versions, I conducted some online research and discovered that certain versions of KeePass 2 were vulnerable to CVE-2023-32784. This vulnerability allowed users to extract the KeePass database master password from a memory dump captured while there was any swap or process data present. This seemed like a promising attack vector.
Exploitation
Step 1:
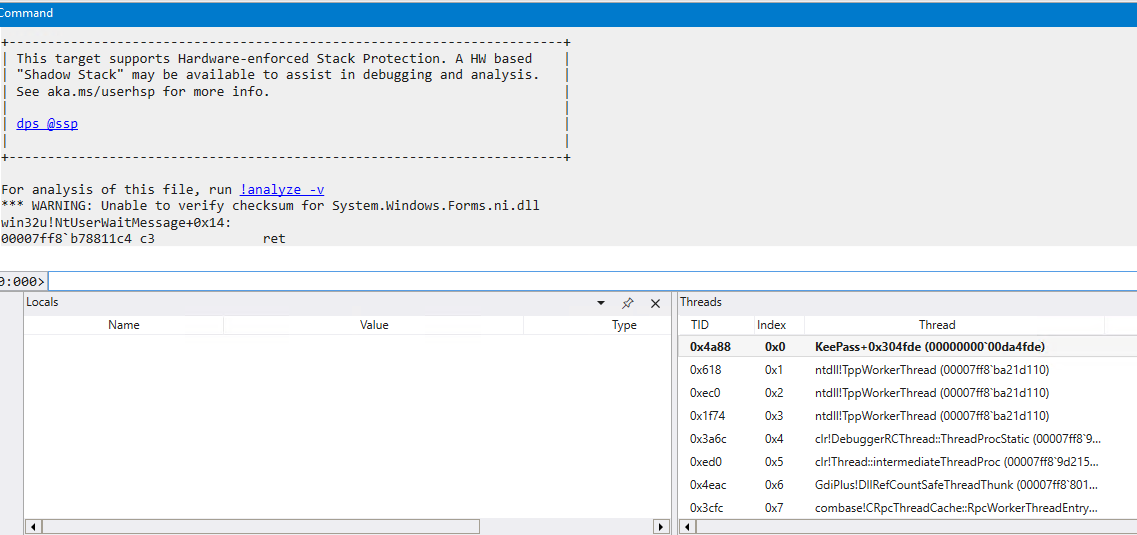
I used WinDBG to inspect the Mini DuMP file and found active KeePass processes inside it.
Step 2:
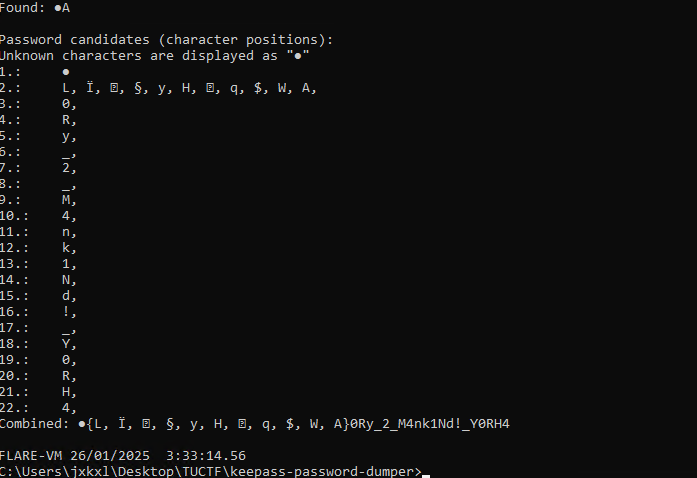
Since this was a CVE, I assumed there would be automated scripts available. I searched GitHub and found keepass-password-dumper. I ran the script and successfully retrieved the password, though the first character was missing. Based on the length of the password, I guessed the first letter was ‘g’—and I was correct.
Step 3:
After logging into the KeePass app, I found two accounts that appeared to be example accounts. While they provided no useful information, I discovered a user named “backdoor_pw” in the recycle bin. Its password was “REDACTEDREDACTEDREDACTED,” which seemed unhelpful at first. However, it contained a suspicious note in hexadecimal format, which looked promising.
Step 4:
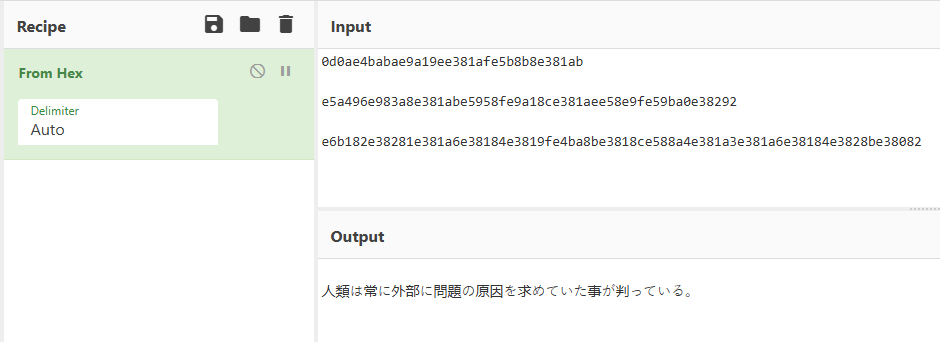
I used CyberChef to decode the hexadecimal string, which resulted in what seemed to be Japanese text.
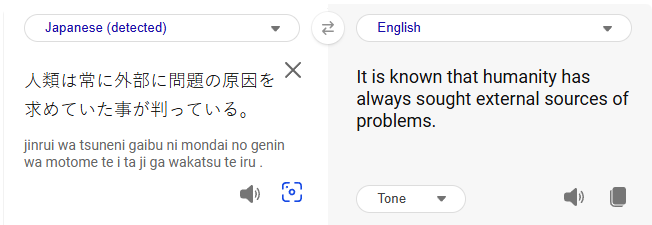
I then turned to Google Translate, but the result was a proverb, leading me to believe this was a dead end.
Step 5:
Returning to the KeePass vault, I checked the password history for the “backdoor_pw” account by navigating to right click > edit entries > history.
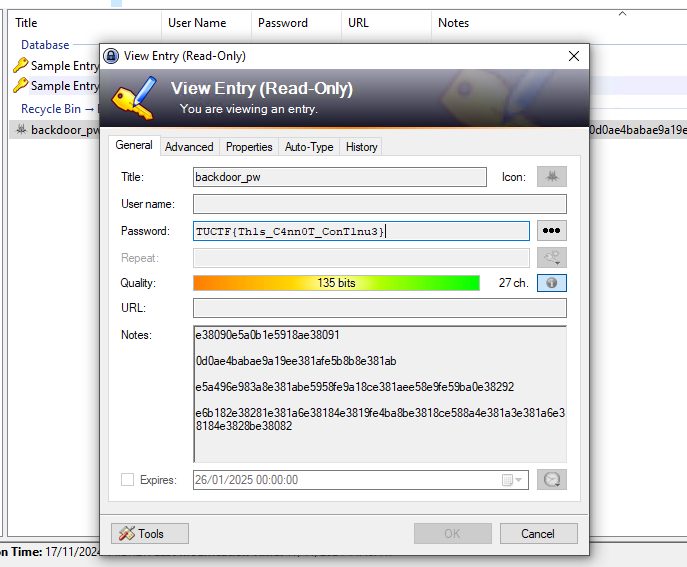
There, I found an original entry for the password: TUCTF{Th1s_C4nn0T_ConT1nu3}.
Solution
- Flag:
TUCTF{Th1s_C4nn0T_ConT1nu3}